The price of knowledge breaches is anticipated to rise from $3 trillion every year to greater than $5 trillion in 2024, reveals “State of Cybersecurity Resilience 2021” report. That clearly explains the necessity for firms to have a well-grounded cybersecurity plan. Whereas that stands true with all the businesses throughout all industries, direct promoting firms have to take additional take care of safeguarding their enterprise in the most effective curiosity of their prospects.
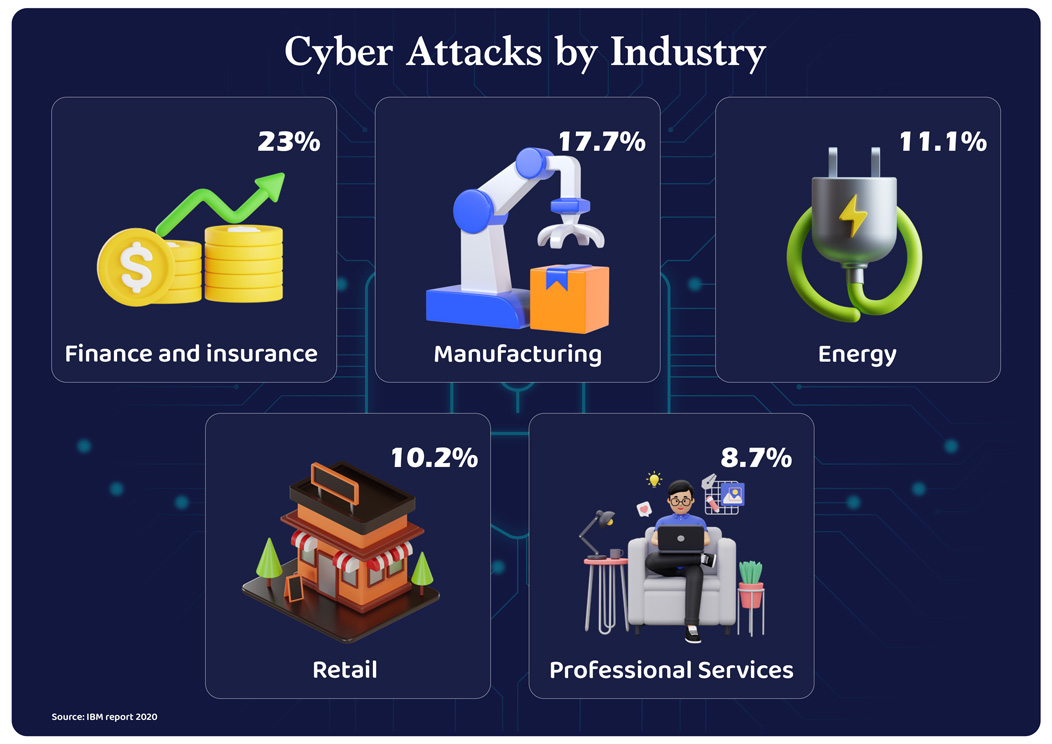
Direct promoting firms retailer prodigious quantities of non-public data of consumers, distributors, and workers. A lean safety framework can show deadly to the enterprise. In the present day, 43% of cyber assaults goal small companies, particularly these within the authorized, insurance coverage, retail, monetary, and healthcare sectors. Companies face cybersecurity accidents when they’re least ready for it. So having a foolproof safety plan in place is the last word weapon to defend the attackers earlier than they even consider focusing on you.

What’s cybersecurity?
Cybersecurity is the observe of defending property that firms and people undertake to safeguard their crucial methods and delicate data from digital assaults. A robust cybersecurity structure can safeguard digital property and essential private and enterprise data.
Earlier than we draft a complete cybersecurity plan, let’s define the potential threats that might block the expansion of your direct gross sales enterprise.
Forms of cyber assaults that may hamper your direct promoting enterprise
In direct promoting, moderately than the monetary data, attackers deal with the private and behavioral data of people both to personally profit from it or to make a fortune by promoting it to the darkish net the place this data is used for malicious causes unknown.
These cyber thugs unleash threats in quite a lot of methods making it laborious for firms and people to defend themselves.
Malware assault
In any other case known as “malicious software program” or “virus”, malware is a program constructed to robotically run unauthorized actions on the sufferer’s system. They assault your system creating malfunction and corrupting your laborious drive or servers. It’s usually delivered over a community or exterior gadgets linked to your system.
Ransomware assault
Ransomware is a type of malware that’s despatched to the goal system both by means of e-mail or different onsite or inapplication downloads. Ransomware holds the system hostage demanding ransom from the sufferer. As soon as the quantity is paid, the attacker handovers the plan to revert the assault. These software program information exploit system vulnerabilities that the corporate or people haven’t addressed. The very fact of the matter is that no antivirus can safeguard or detect ransomware assaults.

Phishing
Phishing assaults are sometimes achieved by means of e-mail the place the consumer is tricked into clicking a hyperlink that exposes your organization data reminiscent of private knowledge, monetary data, and passwords to the attackers. Phishing, being the most typical sort of assault, is concerned in 36% of knowledge breaches, in line with Verizon’s “2021 Knowledge Breach Investigations” report.
Phishing seems in numerous kinds also known as spear phishing or social engineering, whaling, and vishing. In response to PurpleSec, 98% of cybercrime depend on social engineering to perform efficiently.
Cross-site Scripting (XSS)
The attacker injects malicious scripts into web sites seen by victims. It’s meant at gaining unauthorized entry to knowledge, accounts, or purposes. As soon as the entry is obtained the attacker positive aspects full management and might carry out any motion the consumer is permitted to do on the precise web site or utility.
DDoS assaults
Distributed Denial of Service assaults are focused at your web site denying customers entry to your providers. It disrupts the traditional functioning of your web site with spam visitors flooding from a number of distant places.
The frequency of DDoS assaults rose to five.4 million within the first half of 2021 in comparison with the identical interval the earlier 12 months. Within the fourth quarter of 2021, Cloudflare reported a 175% improve within the quantity of ransom DDoS assaults in comparison with the third quarter.
Whereas these are simply the widespread varieties of assaults, these statistics present a transparent perception into the rising density of cyber assaults and the necessity to have an end-to-end safety structure in place.

Growing a direct gross sales cybersecurity technique
One examine by the College of Maryland signifies that there’s a cyber try each 39 seconds. Ever imagined the variety of cyber makes an attempt your companies have to be going through day-after-day? Now that an antivirus or a PCI DSS compliance alone can not meet your concern, try to be up for one thing extra deliberate and robust.
A cyber assault can price firms an awesome deal. A current examine by IBM’s safety division revealed that knowledge breaches now price on common $4 million and the fee per document breached roughly quantities to $158. It’s not simply in regards to the data being stolen however the authorized and monetary penalties that it might incur, the consequence could be devastating. Cybersecurity breaches additionally assault the model belief constructed for years collectively. Each buyer and distributor belief are constructed on the way you safeguard their data and pursuits. As soon as that’s damaged that may actually be the tip of your corporation.
A complete cybersecurity protection to your direct promoting enterprise
We’ve got devised an 8-layered protection plan that can assist you securely handle your direct promoting enterprise in opposition to challenges and threats, and safeguard your buyer pursuits.
Detect system vulnerabilities
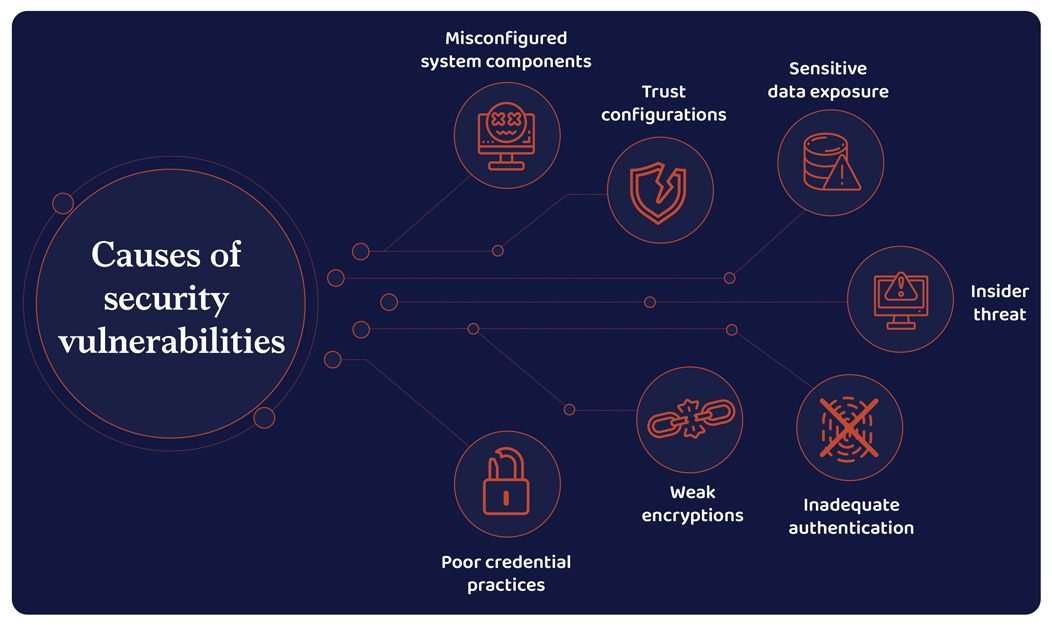
Unattended or unidentified safety vulnerabilities result in interrupted enterprise processes including to the damages prompted to buyer and distributor confidence and ultimately to the group’s repute itself. What organizations should deal with is adopting rapid measures to restrict the injury and weak point eliminated.
At first, firms will need to have a blueprint on how vastly their knowledge is spanned throughout the system. All the time analyze and prioritize safety dangers. Continually monitor your system for vulnerabilities with penetration checks and software program audits. Figuring out and fixing the problems on time may also help mitigate the danger of being focused.
Undertake a zero-trust framework
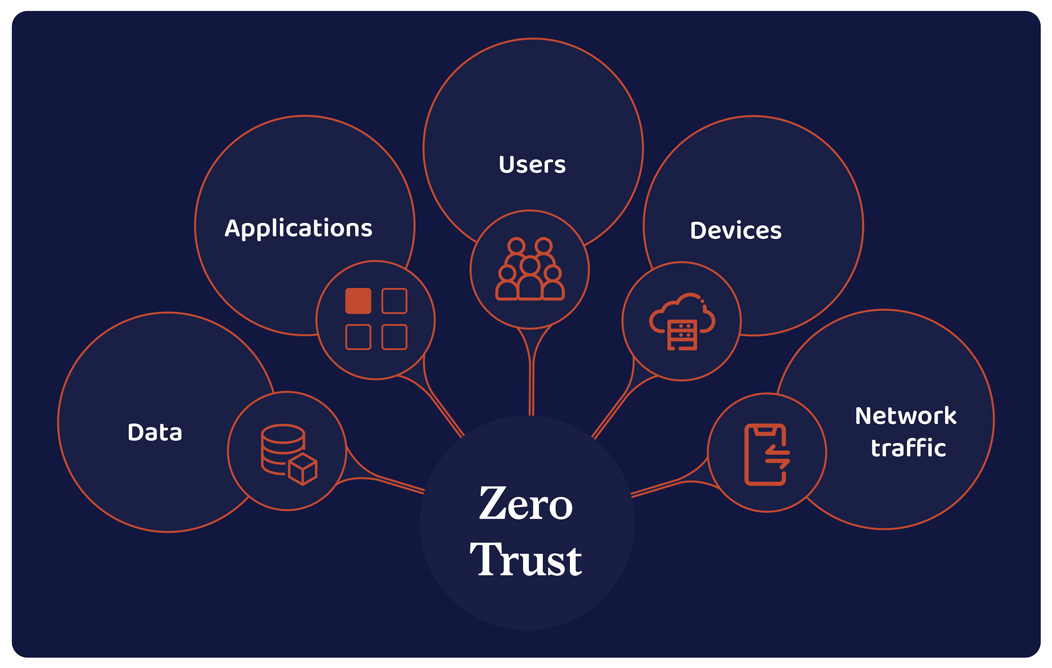
Guarantee solely the suitable individuals have entry to the suitable assets. Safe every part from cell gadgets to servers with authentication. In a examine carried out by Microsoft, The Whole Financial Impression™ of Zero Belief options, implementing a zero-security framework ensures a 50% lowered likelihood of knowledge breach and over 50% improved safety effectivity.
Construct your zero-security structure maintaining your community, endpoints, knowledge, and consumer account safety ranges in thoughts. Define a strict consumer entry coverage to individuals throughout your group.
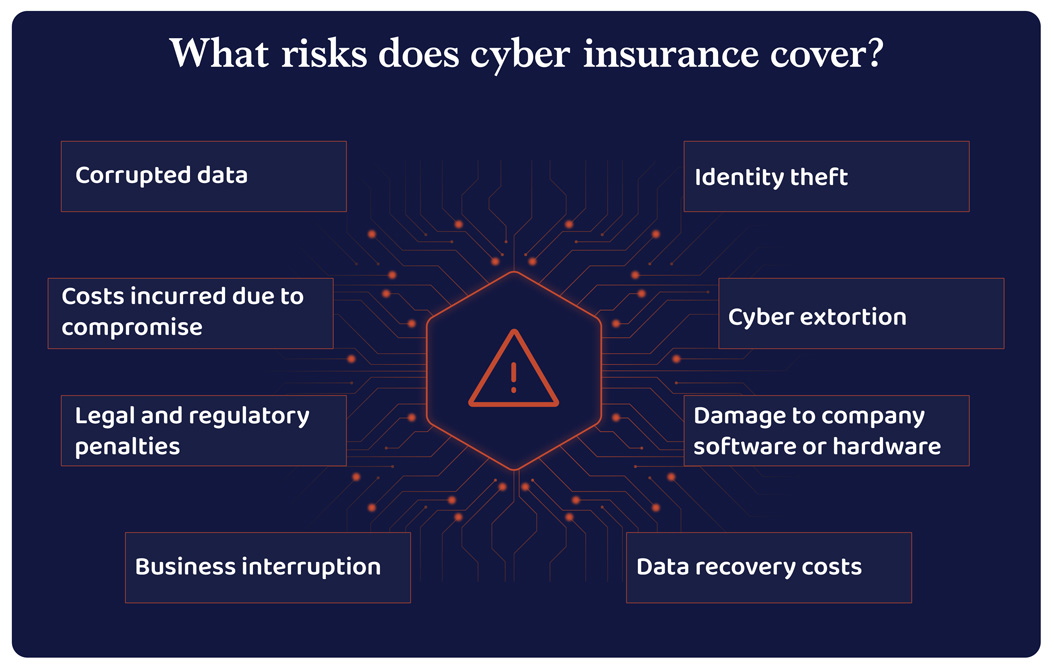
Cyber insurance coverage provides you complete protection of your corporation liabilities together with consumer data, social safety numbers, bank card data, and well being information in opposition to knowledge breaches. Most cyber insurance coverage insurance policies cowl knowledge loss, cyber extortion, fee frauds, pc frauds, and lack of income as a result of breaches.
Cyber insurance coverage helps the corporate’s dedication and accountability to keep up regular compliance and regulatory commonplace in dealing with massive quantities of consumer data.
Educate your individuals to detect potential threats
A big a part of your group is working remotely. Flexibility comes with an elevated fee of danger related to it. Distributors entry your system from places unknown and that will increase your possibilities of being uncovered to cyber assaults.
Conduct safety consciousness coaching applications and prepare them on the group’s safety protocol with mock threats and stealth checks. Implement periodic password adjustments and encourage them to make use of safe log-on processes.
Instill cybersecurity as a accountability moderately than an obligation.
Allow multi-factor authentication
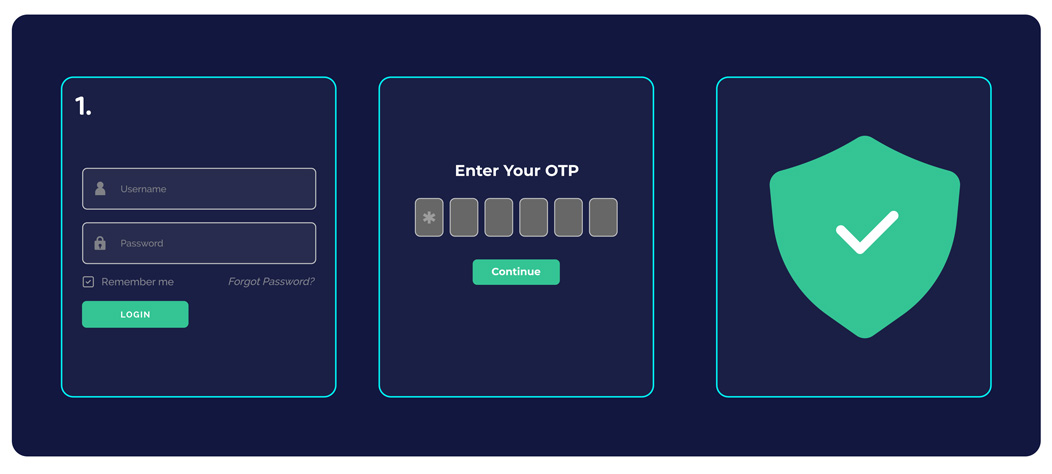
Multi-factor authentication is a foundational cyber protection mechanism in growing a robust cyber safety plan. This enforces strict multi-layered authorization measures earlier than granting entry to methods or databases.
Multi-factor authentication must be carried out throughout all methods, networks, and purposes throughout the group. Identification and Entry Administration methods (IAMs) additionally act as an efficient approach for directors to observe and establish suspicious on-line exercise in a cloud-based atmosphere.
Carry out penetration checks
When cyber safety challenges are rising in quantity, dimension, and kinds, organizations are compelled to undertake a cybersecurity plan that helps defend themselves no matter their dimension. Penetration testing turns into an integral a part of a complete cybersecurity technique for the truth that it helps organizations detect loopholes of their present cybersecurity plan.
Throughout penetration testing, mock assaults are carried out to detect vulnerabilities brought on by {hardware} or software program design flaws, inefficient password administration, or compromises made by human intervention. Penetration testing must be carried out on all group networks, purposes, {hardware}, software program, and consumer conduct.
Risk intelligence assist firms leverage the ability of knowledge to make security-backed risk selections and construct efficient protection mechanisms. This predictive functionality helps establish attackers and reply sooner to risk incidents. Risk intelligence is delivered by means of implementing the suitable instruments, methods, and procedures (TTPs).
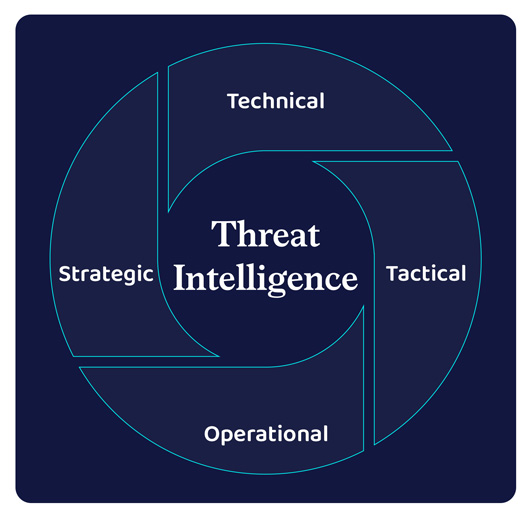
Risk intelligence is employed in 4 kinds—tactical, technical, strategic, and operational. Whereas tactical risk intelligence identifies easy indicators of compromises reminiscent of malicious IPs, URLs, or domains, technical risk intelligence devises a defensive mechanism primarily based on clues or proof derived from earlier assaults reminiscent of reported IP addresses, the content material of phishing emails, malware samples, and fraudulent URLs, to establish the potential of future assaults.
Each strategic and operational risk intelligence wants human intervention to be absolutely succesful. Strategic risk intelligence delivers insights into the threats, preventive measures, and severity of the threats to the group’s cybersecurity workforce. Operational intelligence analyzes the who, why, and the way of assaults and gives organizations with a sensible view of potential assaults.
Create a cell incident response plan
Typically neglected, cell gadgets additionally pose critical safety points for a company. Cellular gadgets are extra vulnerable to knowledge breaches and cyber threats. Therefore together with them within the cybersecurity structure is of prime significance.
Firms should create an actionable incident response plan to safeguard the system earlier than exploitation. As a primary step to drafting an incident response plan, organizations should define the scope of incidents and methods to detect and include threats. A compact incident response plan should additionally define strategies to eradicate dangers, restore methods, and continually monitor to mitigate dangers.
Client Sentinel Community, an investigative cyber software by FTC, analyzed over 5.7 million experiences within the 12 months 2021 out of which 49% had been fraud and 25% constituted identification theft. Whereas each circumstances are critical causes for concern most firms again out contemplating the fee concerned in implementing a robust cybersecurity structure. If that’s in your thoughts then what it is best to know is {that a} single assault of any sort, be it an information breach, malware, ransomware, or DDoS assault, prices firms of all sizes a median of $200,000, and plenty of affected firms exit of enterprise inside six months of the assault, in line with insurance coverage firm Hiscox.
So, what’s your cybersecurity plan?




