To achieve your prospects’ inboxes with e-mail advertising and marketing campaigns, your area needs to be a trusted supply. In any other case, your messages will find yourself hitting the spam folder and stay unnoticed. And e-mail authentication helps keep away from this.
So what’s e-mail area authentication, why it issues, and what e-mail authentication protocols are there? Let’s talk about this.
What’s e-mail authentication?
Electronic mail authentication is a apply that means validating a sender’s e-mail deal with to verify that it’s approved to ship emails from a selected area. It additionally helps affirm that the area belongs to a sure Mail Switch Agent (MTA) approved to switch an e-mail.

(Supply: Selzy)
So, placing it merely, e-mail authentication helps affirm that the sender is who they are saying they’re. This validation helps establish spammers and disable them from sending out emails.
Why is it essential?
Having found out what e-mail authentication is, let’s dive into why it issues. Electronic mail authentication enhances your area’s safety by confirming to servers that your emails come from a legitimate supply. This, in flip, prevents your model from fraud and impersonation.
Since authentication prevents the malicious exercise out of your area, it will get a trusted fame amongst ISPs. This reveals that you’re a dependable and credible sender and, most significantly, maintain your e-mail deliverability at an excellent stage.
In the long term, area safety and a excessive e-mail deliverability fee contribute to the belief in your model and a optimistic model picture.
Electronic mail authentication protocols
Understanding what e-mail sender authentication is shouldn’t be sufficient — the core of the method lies within the e-mail authentication strategies or protocols. These are completely different from e-mail protocols, those which might be used for SMTP or IMAP servers. So let’s talk about SPF vs. DKIM vs. DMARC protocols, what they’re, and the way they differ.
(Supply: ZetaGlobal)
SPF report
SPF stands for Sender Coverage Framework and is a listing of IP addresses inside a site. These addresses are approved and, subsequently, allowed to ship emails. An SPF report is available in a .txt file and is current in a sender’s Area Identify System (DNS). SPF is a extensively adopted protocol for e-mail authentication.
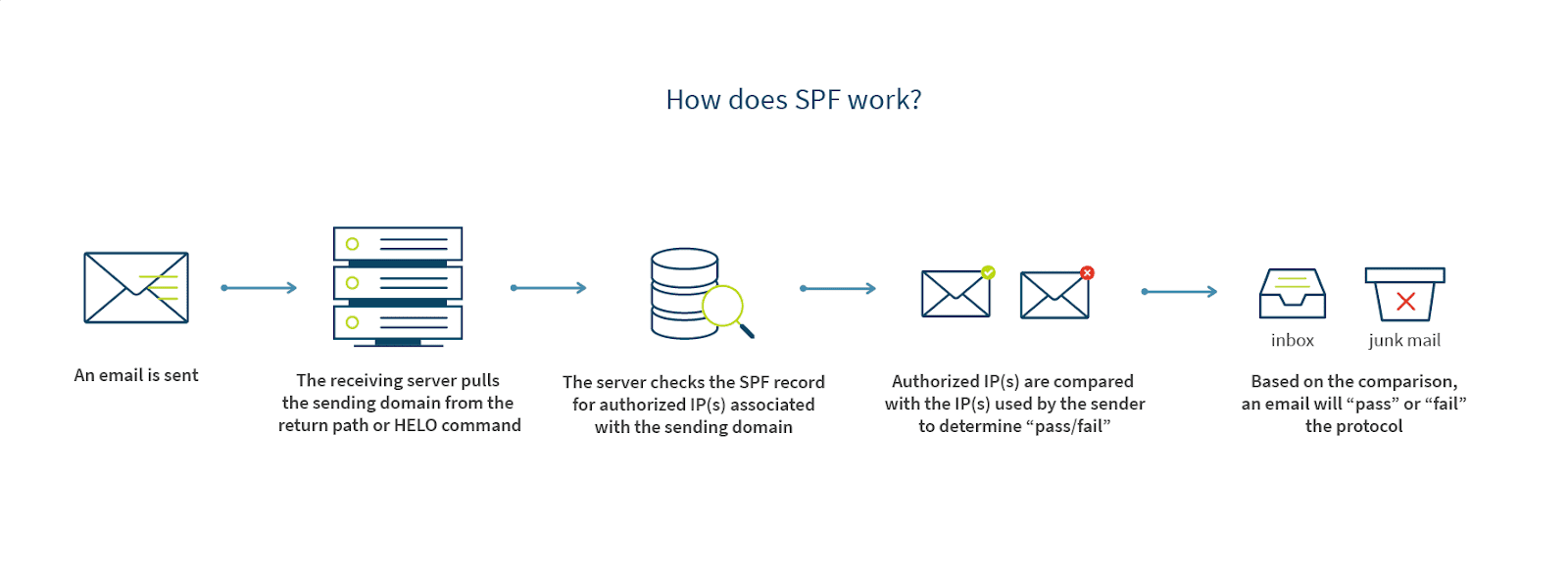
(Supply: ZetaGlobal)
So once you ship an e-mail and it reaches the recipient’s server for incoming emails, the SPF e-mail authentication runs a examine. It’s a DNS search that goes by all of the SPF information. In case your e-mail deal with is discovered in the course of the search, then the e-mail proceeds to the recipient’s inbox. In any other case, it’s rejected and won’t be despatched additional.
Finest practices for SPF
SPF has completely different qualifiers — they convey with the server concerning what to do with a selected IP deal with. The qualifiers are:
- + — a Move, that means that the IP deal with has handed the check and the e-mail could be accepted;
- – — a Onerous Fail, that means that the IP has failed the check and the e-mail ought to bounce;
- ~ — a Comfortable Fail that alerts for a failed check; the e-mail is accepted however marked as failed;
- ? — a Impartial check outcome (not a fail, not a go), and almost certainly, the e-mail is accepted, though it may be rejected.
Whereas these are fairly definitive, the qualifiers are simply ideas on what the server ought to do to an e-mail in order that they are often ignored. For instance, an e-mail with a Move could also be despatched to spam, whereas a Onerous Fail one could be accepted.
Often, the qualifier appropriate for many e-mail senders is Comfortable Fail. This can make sure that all of your emails are despatched however shall be marked as “SPF failed” in case they fail. The Impartial coverage is one other frequent selection.
As a result of Comfortable Fail accepts all of your emails, you’ll protect your e-mail deliverability fee whereas utilizing SPF. On the similar time, you don’t must sacrifice safety as a result of all of the suspicious emails shall be marked as such.
DMARC report
DMARC stands for Area-based Message Authentication Reporting and Conformance. This e-mail authentication protocol provides area house owners quite a lot of energy over how their failed messages are handled on the recipient’s incoming server.
DMARC offers an extra stage of safety constructed on prime of different protocols, which is known as area alignment. This makes the report extraordinarily efficient in stopping spoofing, impersonating, and different malicious habits.
DMARC can also be mixed with different protocols, making certain most safety. Utilizing a single protocol is inadequate to make sure that all of your emails attain their recipients properly, and DMARC helps deal with emails that failed SPF or DKIM insurance policies.
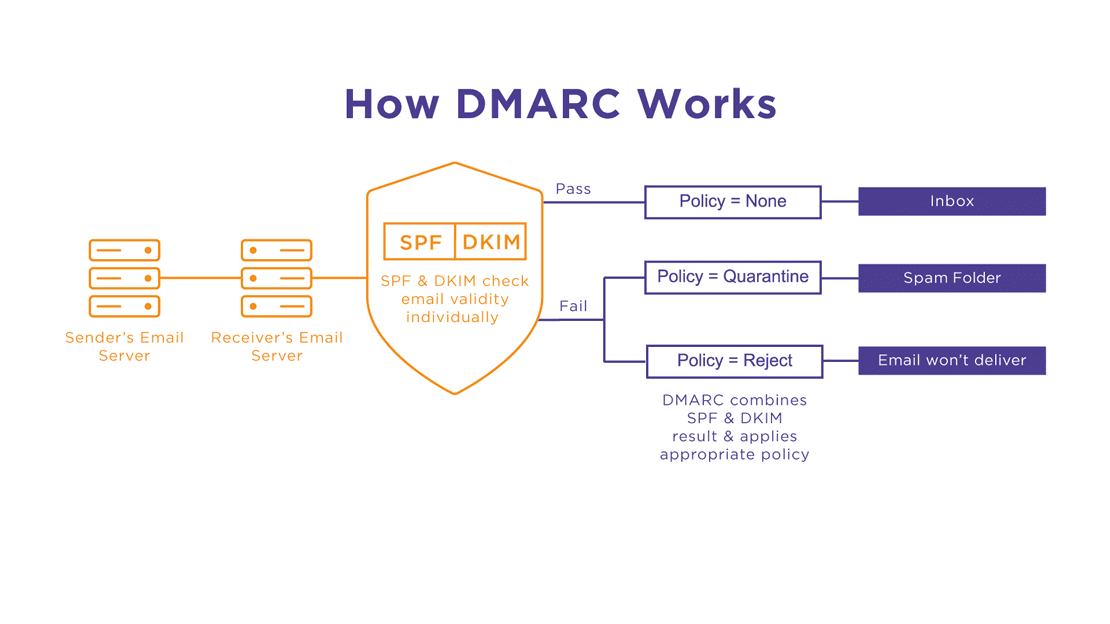
(Supply: Agari)
Moreover the listed capabilities, DMARC additionally permits receiving studies from the servers in your emails’ efficiency and deliverability. This provides you a chance to determine the the reason why your emails fail and troubleshoot in time. Finally, DMARC helps maintain a gentle e-mail deliverability and builds belief in your model.
Finest practices for DMARC
As already talked about, DMARC permits directing the server concerning what to do with failed emails. Specifically, there are three insurance policies you possibly can select from to determine learn how to deal with your failed emails:
- reject — discard emails;
- quarantine — permit emails however ship them to the spam folder;
- none — do nothing.
The final coverage implies that the failed emails are handled as if there was no DMARC arrange. So primarily based on different standards, the e-mail could be accepted, despatched to the spam, or discarded.
Whereas the “None” coverage could seem helpful, it helps with marketing campaign monitoring and report evaluation with out negatively impacting authentic emails and general e-mail deliverability. That is additionally the really helpful coverage to decide on if you happen to’re beginning with DMARC to get the hold of the way it works.
Moreover, you possibly can select what share of your failed emails the coverage ought to apply to utilizing the “pct” tag, which might set the remainder of the messages to “None.”
Talking of area alignment, it may be set to “Strict” or “Relaxed.” “Relaxed” is greatest if you happen to ship emails through exterior providers (an e-mail service supplier). As a result of “Strict” area alignment implies that the sending and returning addresses are the identical, DMARC would fail if you happen to ship your emails from a no-reply e-mail deal with.
DKIM report
DKIM stands for DomainKeys Recognized Mail and is one other commonplace protocol for e-mail authentication, additionally efficient for phishing prevention.
The DKIM report incorporates an encryption key and a cryptographic signature which might be used to validate the e-mail deal with with a public key on the recipient’s finish. Equally to SPF, the report is saved as a .txt file within the sender’s DNS.
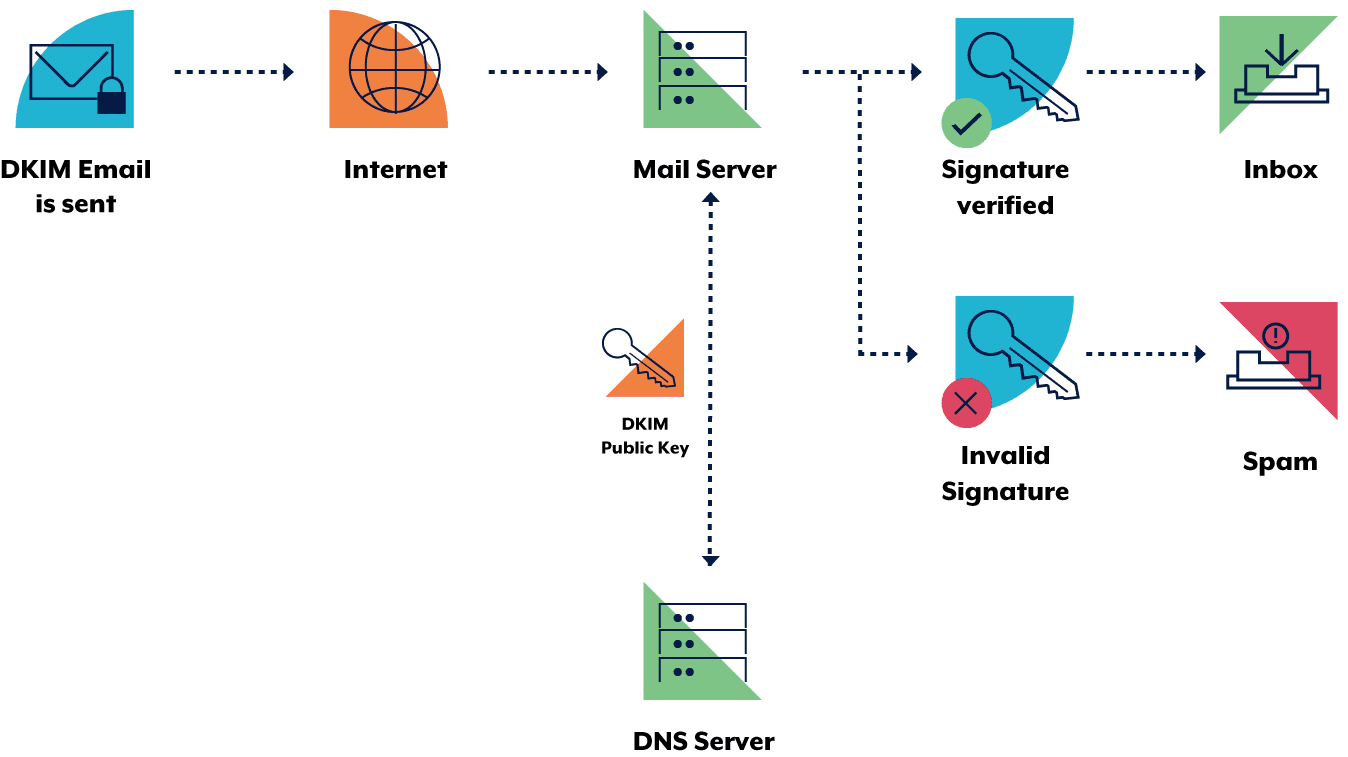
(Supply: Australian Cyber Safety Centre)
The DKIM protocol encrypts a site’s key for e-mail authentication in 3 steps:
- The sender creates a DKIM signature by figuring out what fields (i.e., their e-mail deal with, message physique, and so on.) to incorporate.
- The e-mail system creates a hash string of chosen textual content fields.
- The hash string is encrypted with a personal key that solely the sender can entry.
To authenticate an e-mail deal with, the server seems to be for a match between the non-public and public keys within the DMS. If there may be one, the DKIM signature could be decrypted again to the hash string, and the e-mail is delivered. And in case there isn’t any match, the DKIM check fails, and the e-mail is almost certainly discarded.
Finest practices for DKIM
Moreover the absence of a match between non-public and public keys, DKIM checks can fail for different causes. To keep away from DKIM failures, keep away from instances like the next:
- the fields within the hash string are modified whereas the e-mail is in transit;
- the non-public key size is shorter than 1024 or 2048 bits; another lengths are now not supported;
- the DNS zone of the sender’s area shouldn’t be accessible for search, which is a frequent situation with poor internet hosting suppliers.
To maintain the DKIM report safe and efficient, it’s important to run common updates of personal and public keys. By updating your keys a couple of times a yr, you stop any dangers of sending out spam out of your area.
When altering the keys, make sure that to have two signatures accessible — some emails should be in transit, and altering each keys with a single signature will result in a DKIM examine failure. However if in case you have a number of signatures, one will go even when the opposite fails.
DKIM report can also be essentially the most appropriate one for e-mail auto-forward. Once you use ESPs, DKIM doesn’t think about it a failure that the sender’s and return e-mail addresses differ (like SPF). It is because the signature is assigned to the e-mail physique, which stays unchanged throughout auto-forward.
Do you have to use all e-mail authentication protocols?
After studying what e-mail authentication is, you almost certainly now perceive the significance of mixing completely different e-mail protocols. DMARC, DKIM, and SPF deal with area authentication in very other ways, which implies utilizing just one protocol gained’t cowl all of your authentication wants.
So as a result of every protocol runs checks in a different way, utilizing a number of or all three strategies provides the very best area safety and e-mail deliverability fee.
How you can check e-mail authentication?
There are numerous methods to check your e-mail authentication, each manually and routinely. To run a handbook examine, ship your check e-mail to a Gmail person, click on “Extra” on the obtained e-mail, and choose “Present unique.” You will note a brand new window with SPF, DKIM, and DMARC examine outcomes. If they’re “PASS,” then your area is authenticated.
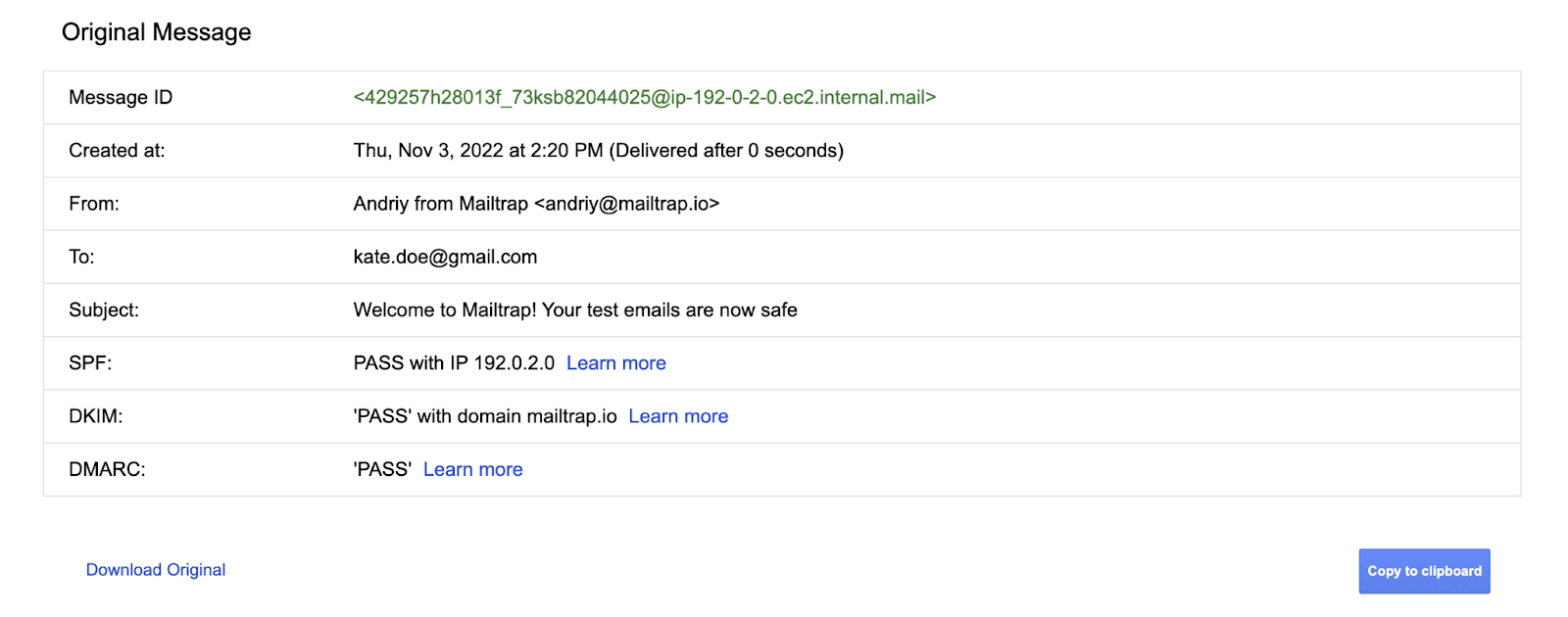
(Supply: Mailtrap)
You too can discover quite a lot of instruments for automated e-mail authentication checks, like DMARC Analyzer, which checks for all three protocols, DNS Checker, DKIM Wizard, and different single protocol checkers.
With Postmaster Instruments by Gmail, you possibly can examine your e-mail efficiency, establish supply errors, and analyze detailed spam studies. You might want to have a Google account to trace information and look at quite a lot of informative dashboards.
One other device that automates your e-mail authentication and runs common checks for you is Mailtrap Electronic mail API. It verifies your area by all three protocols and updates DKIM keys routinely each 4 months. With this device, you possibly can all the time make certain that your area is authenticated.
Wrapping up
Electronic mail authentication is area verification, which confirms its reliability and safety and helps maintain e-mail deliverability excessive. Authentication is run utilizing three sorts of protocols: SPF, DMARC, and DKIM information. Whereas every protocol can authenticate your area, it’s greatest to make use of three information altogether to make sure that your e-mail deal with is authenticated always.
Be part of Stripo to design lovely emails effortlessly



